Configuring Google Authenticator SSH on CentOS 7 aka 2-factor authentication brings more safety and security to VPS administration as well as your data. In this article, TopHostCoupon will show you how to enable 2-factor authentication when SSHing into your system.
What is 2-factor authentication?
2-Factor Authentication, or 2FA (Two-Factor Authentication) for short, is an extra step in your normal login activity. Without 2FA, you will only enter your username and password to log into the system, your account. The password section will be the only layer of protection for the account. Meanwhile, the added second layer of security will help you better protect your account.
Why should use 2-layer security?
2-layer security is the best way to protect yourself from attacks that steal sensitive user account information, spoof login pages, and other account hijacking methods. With 2-layer security, you can be more assured if your account information is accidentally exposed, then it will be difficult for others to access your accounts because it will be hindered in the 2-layer security step. .
In this article, TopHostCoupon will show you how to set up 2-factor authentication when SSHing into your VPS server, this helps increase the security of your VPS if your root information is accidentally exposed. For detailed steps, please see below!
Install Google Authenticator SSH on CentOS 7
To set up Google Authenticator, you can follow these 4 steps.
Step 1: SSH into your server
First, you need to SSH into your VPS with Root rights, if you don’t know how to SSH, you can see the instructions below.
After SSH is successful, you continue to see Step 2.
Step 2: Set up Google Authenticator
Install the epel-release repo
yum install -y epel-release
Next need to install google-authenticator package
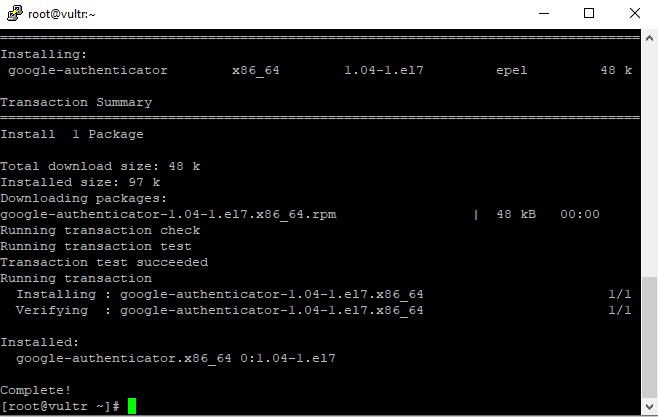
yum install -y google-authenticator
Install Google Authenticator package successfully
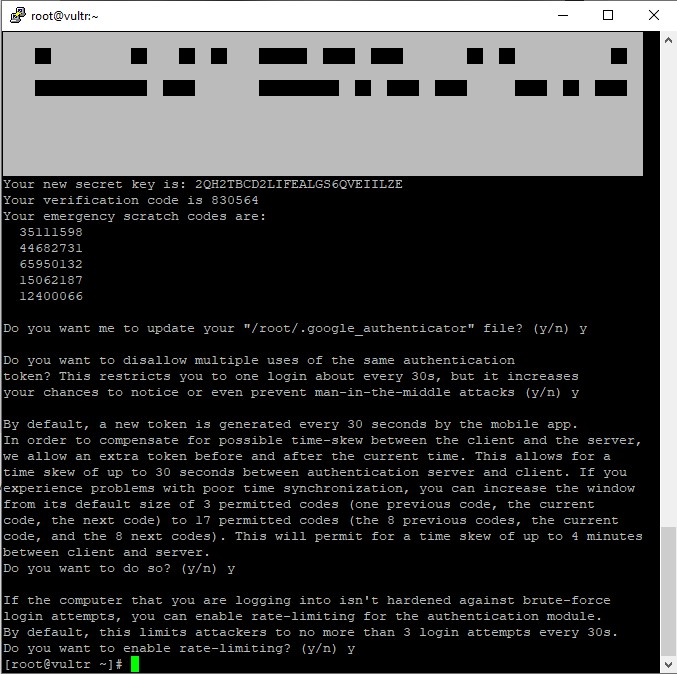
Run the following command after the installation is complete to generate the secret key.
google-authenticator
Next, the system will ask you to confirm and provide a QR code
Open the Google Authenticator app on iOS or Android and scan the QR code displayed on your VPS
Step 3: Set up VPS to allow authentication through Google Authenticator
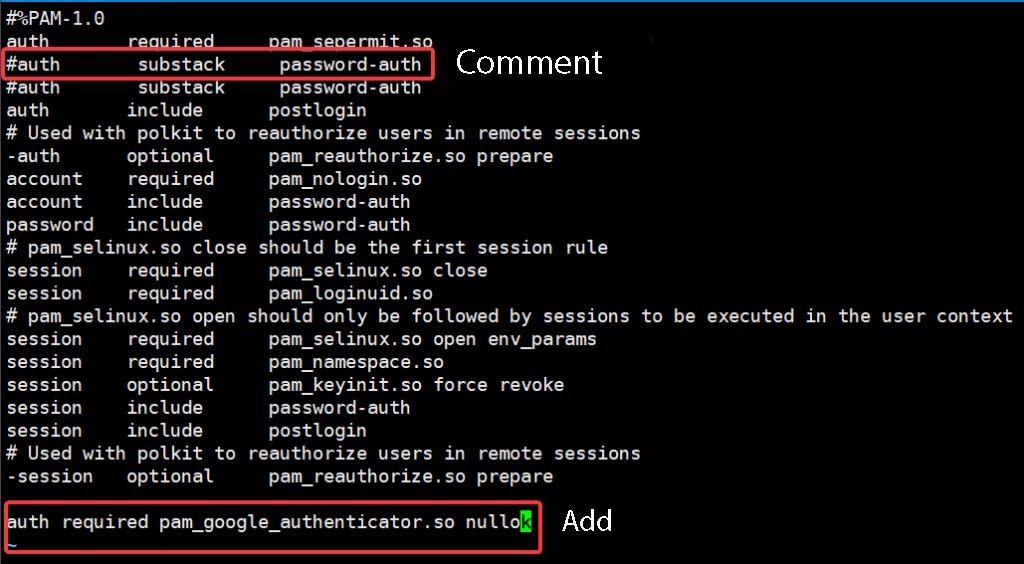
To set up VPS to allow Google Authenticator authentication when SSH, you move and edit the file /etc/pam.d/sshd
Add and commend the following lines in the file /etc/pam.d/sshd
Add: auth required pam_google_authenticator.so nullok
Comment: auth substack password-auth.
Proceed to edit the file /etc/ssh/sshd_config
Find the line ChallengeResponseAuthentication, change the setting from no to yes
Add new line AuthenticationMethods publickey,keyboard-interactive
Restart the sshd service after editing.
systemctl restart sshd
Step 4: Check the operation of Authenticator when SSH
After completing the configuration, you need to exit the VPS and log in again to check. When Login OTP code will be generated on Google Authenticator App, you just need to enter the code to be able to SSH.
So in this article, TopHostCoupon showed you how to install 2-factor authentication when SSHing into VPS, this helps to increase security and reduce the risk of password detection attacks. With 2-factor authentication, you can rest assured that even if your root information is accidentally exposed, others will not be able to SSH into your VPS without the 2-factor authentication code.